Authentication and User Management
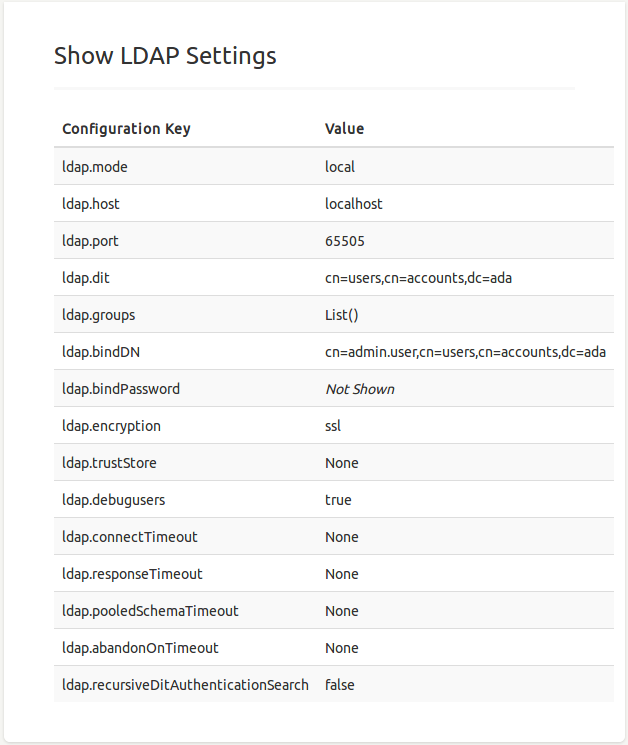
LDAP Settings
Ada does not store any passwords but rather relies on LDAP for authentication.
Several LDAP settings are available, which all start with the ldap prefix (e.g. ldap.dit):
- host
refers to the host of an LDAP server. Defaults to
localhost. Normally set by the environmental variableADA_LDAP_HOST(inset_env.shfor production). - port
of the LDAP server. Defaults to
389. - bindDN is the DN for the bind operation.
- bindPassword
is the password for the bind operation. Normally set by the environmental variable
ADA_LDAP_PASSWORD. - dit
is the LDAP root directory used for authentication. In particular, the
ditis combined with an user id as a suffix:uid=$id,$ditthat is passed to LDAP together with a password during authentication. - groups
are the names of the LDAP groups (defined as a sequence), in which the requested Ada users reside. Note that this setting is used solely for an automatic import of users form LDAP to Ada. Defaults to
[]. - mode
of the LDAP server with possible values:
remoteto use a (normal) standalone remote server,localto start an in-memory local server, andnoneto disables LDAP completely. Defaults tolocal. - debugusers
indicates whether debug users (
adminandbasic) should be enabled. Defaults tofalse. Warning: once enabled the admin and basic users can log in without any authentication using/loginAdminand/loginBasicendpoints, which is fine for local (restricted) deployments but should be absolutely avoided for public use! - encryption
used for the LDAP connection. Can be either
ssl,starttls, ornone. Defaults tonone, which means client certificates are disabled and server certificates are always trusted. - trustStore is a location of certificates from trusted Certificate Authorities (optional).
- connectTimeout in milliseconds (optional).
- responseTimeout in milliseconds (optional).
- pooledSchemaTimeout in milliseconds (optional).
- abandonOnTimeout in milliseconds (optional).
- recursiveDitAuthenticationSearch
if set to
truean LDAP sub-search authentication is enabled. This experimental feature first traverses all sub entries of theditpath. If it finds a requested user it feeds its path (as a suffix) for the authentication together with the user id. Defaults tofalse.
In nutshell, there are two basic scenarios:
1. if you don't have an LDAP server, don't need authentication, and want to use dummy admin and basic users you can simply set the following lines in custom.conf:
ldap {
mode = "none"
debugusers = true
}
or
ldap {
mode = "local"
port = "65505"
debugusers = true
}
2. If you have an existing LDAP server you want to authenticate against you need to configure the host and bind password environmental variables in set_env.sh
export ADA_LDAP_HOST="ldap.north.edu"
export ADA_LDAP_BIND_PASSWORD="XXX"
and set the following lines in custom.conf
ldap {
dit = "cn=accounts,dc=north,dc=edu"
groups = ["cn=ada-group,cn=groups,cn=accounts,dc=north,dc=edu"]
bindDN = "uid=ldap-reader,cn=users,cn=accounts,dc=north,dc=edu"
}
or without environmental variables (purely in custom.conf) as
ldap {
host = "ldap.north.edu"
dit = "cn=accounts,dc=north,dc=edu"
groups = ["cn=ada-group,cn=groups,cn=accounts,dc=north,dc=edu"]
bindDN = "uid=ldap-reader,cn=users,cn=accounts,dc=north,dc=edu"
bindPassword = "XXX
}
The currently used LDAP settings can be reviewed by clicking on LDAP Settings located in the Admin menu (see the screenshot on on the right).
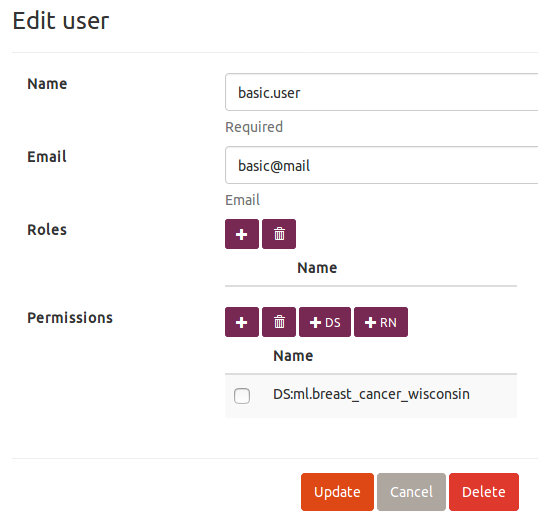
Basic User Management
User management actions admins can conveniently perform:
-
Filter Users by Permission by
Admin → Users → Actions → Filter by permissionand entering a permission prefix. This function is especially handy if you want to obtain a list of all the users who have access to a certain data set, in which caseDS:[data set id]must be entered (see the section Permissions bellow).
Permissions
Admins have access to all the data sets and can perform all the actions throughout the application. On the other side, all non-admin users need to have explicitly assigned permissions to able to access specific data sets, perform specific actions on those data sets, and execute runnables. Note that basic users can not execute or manipulate any data set imports or transformations, or manage other users' permissions (obviously).
For Data Sets
All data set permissions start with DS: prefix and can be fine grained to the level of individual actions following the hierarchy: DS:[data set id].[controller].[action].
[controller] corresponds to an actual web controller, which serves actions for the tabs or menu options in the top bar:
-
dataSet: Views and Analytics -
field: Dictionary -
category: Categorical Tree -
filter: Setting → Filters -
dataview: Setting → Views -
classificationRun: Analytics → ML Classification → Standard -
regressionRun: Analytics → ML Regression → Standard -
temporalClassificationRun: Analytics → ML Classification → Temporal -
temporalRegressionRun: Analytics → ML Regression → Temporal
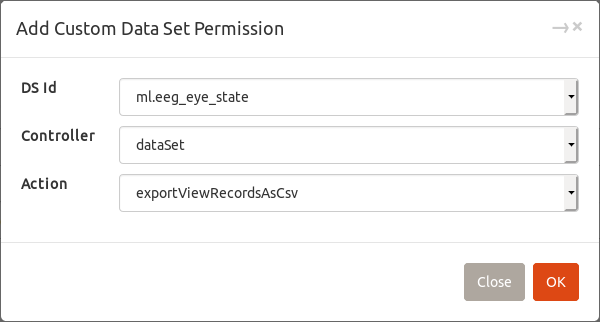
 → Custom
→ CustomALL can be selected as a controller or action.Examples:
-
DS:ml.eeg_eye_state.dataset.exportViewRecordsAsCsvgives a user right toexportViewRecordsAsCsvfor the data setml.eeg_eye_state. -
DS:ml.eeg_eye_state.classificationRungives a user right to invoke any actions of the controllerclassificationRunof the data setml.eeg_eye_state. -
DS:ml.eeg_eye_stategives a user full rights to perform any action (of any controller) on the data setml.eeg_eye_state. Note thatSetting → Generalis accessible only for admins and also each user can edit (or delete) only the filters and views that he/she created.
In a nutshell, there are three common permission scenarios facilitated by the following functions:
-
Standard(recommended) - invoked by → Standard
→ Standard
All standard actions are allowed: views, analytics, filters, and views, but no metadata manipulation (e.g., dictionary and categorical tree) and no ML. In particular, the individual permissions/actions are:dataSet field.find category.idAndNames dataview filter -
View-Only- invoked by → View-Only
→ View-Only
User can only see already existing views and filter them. The allowed actions are:dataSet.getView dataSet.getDefaultView dataSet.getWidgets dataSet.getViewElementsAndWidgetsCallback dataSet.getNewFilterViewElementsAndWidgetsCallback dataSet.generateTable dataSet.getFieldNamesAndLabels dataSet.getFieldTypeWithAllowedValues dataSet.getCategoriesWithFieldsAsTreeNodes dataSet.getFieldValue dataview.idAndNamesAccessible filter.idAndNamesAccessible -
All- invoked by → Custom
→ CustomALLas a controller.
User can perform all actions for a given data set.
For Runnables
All runnable permissions start with RN: followed by the full name of a selected runnable class: RN:[runnable class name]. Such permission allows a given user to execute the runnable.
Runnable permissions can by assigned by choosing  and selecting a desired runnable name.
and selecting a desired runnable name.